Understanding and Monitoring Embedded Web Scripts
Thursday, March 26th, 2015Modern web applications make frequent use of third-party scripts, often in ways that allow scripts loaded from external servers to make unrestricted changes to the embedding page and access critical resources including private user information. Our paper describing tools to assist site administrators in understanding, monitoring, and restricting the behavior of third-party scripts embedded in their site, and what we’ve learned by using them, is now available: Yuchen Zhou and David Evans, Understanding and Monitoring Embedded Web Scripts, IEEE Symposium on Security and Privacy 2015.
Yuchen will present the paper at the Oakland conference (in San Jose) this May.
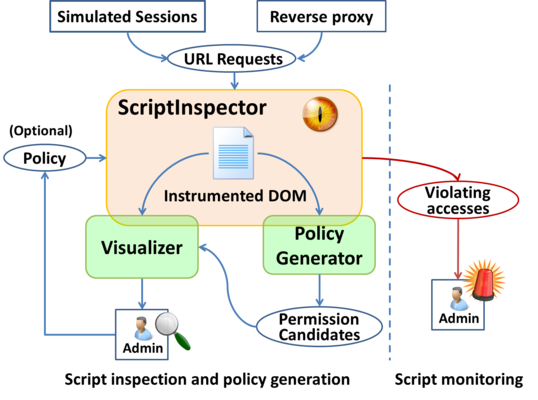
Project Site: ScriptInspector.org
